Samsung has been developing its own home automation system called SmartThings for years. In 2020, Samsung told that the system had been integrated with Mercedes car computers, and in 2023 it was compatible with Matter standard that aims at making … Read the story...
Category: Security
Secure your web browser for privacy and stop cybercriminals
Everyone who has a phone, tablet or PC uses a web browser more than she realizes. In many cases, banking, paying purchases with a credit/debit card, booking health related appointments, reading news, watching movies, and many more services are available … Read the story...
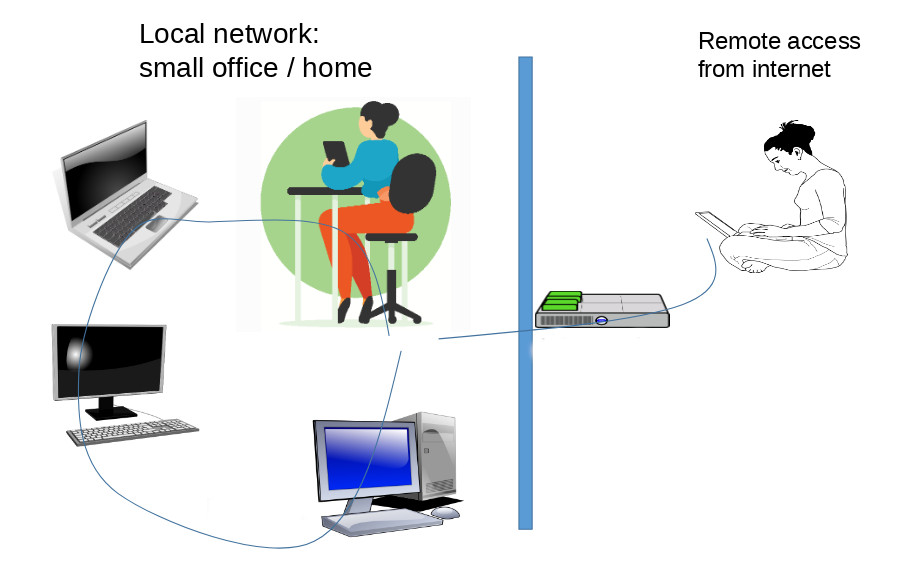
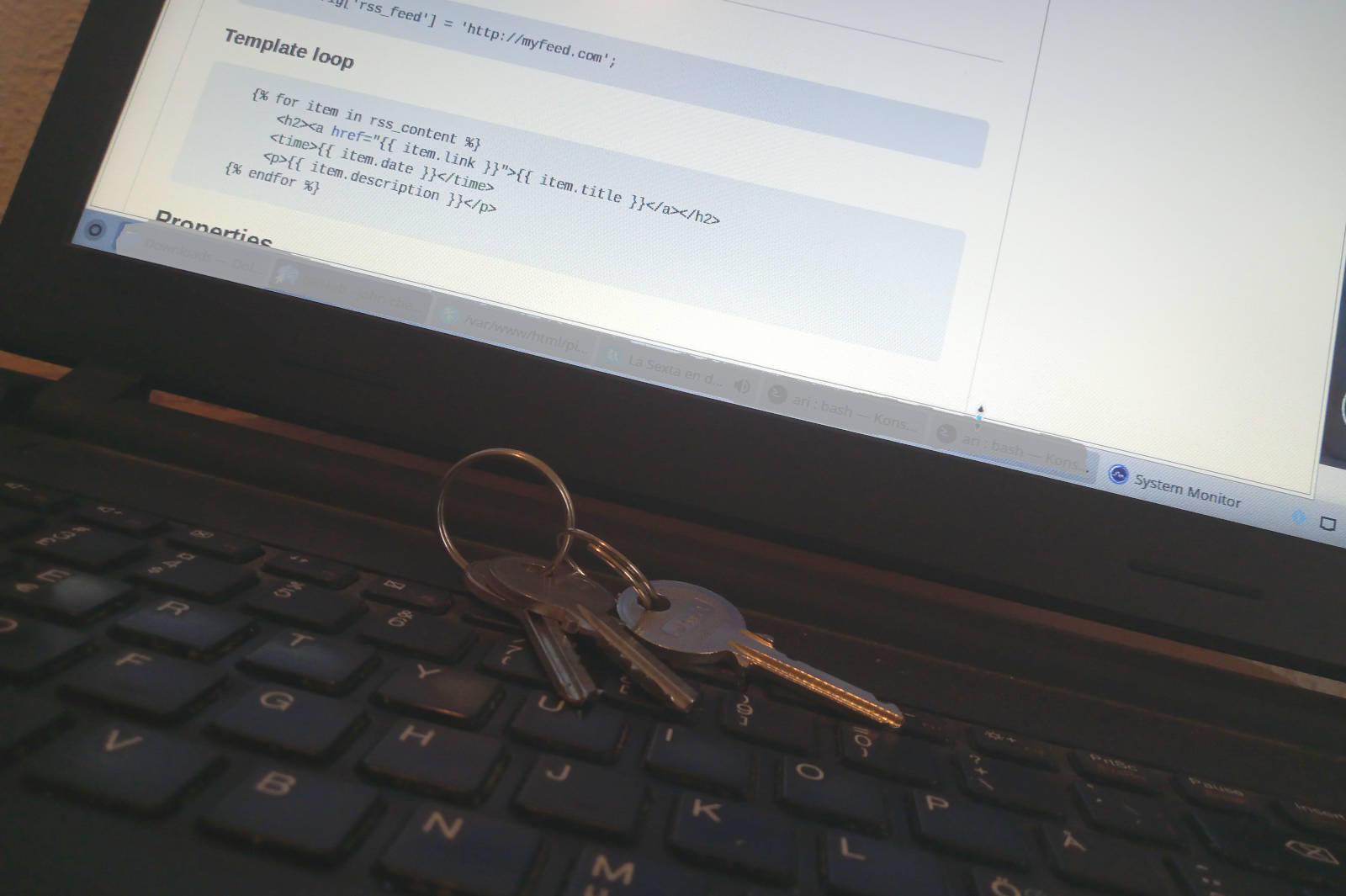
How to install and configure Dnsmasq for your network – remote access option included
Our home office network had gradually grown to the point that no one could remember the IP addresses of all devices. All the connected PCs, phones, tablets, and other devices had to be assigned names so that, for instance, a … Read the story...
Modern cars have become personal data collection machines
Since 2018, when the renowned cybersecurity expert Bruce Schneier tried (and failed) to buy a new car in the US that would come without internet connection, I have worried about the personal data automakers will be collecting from our … Read the story...
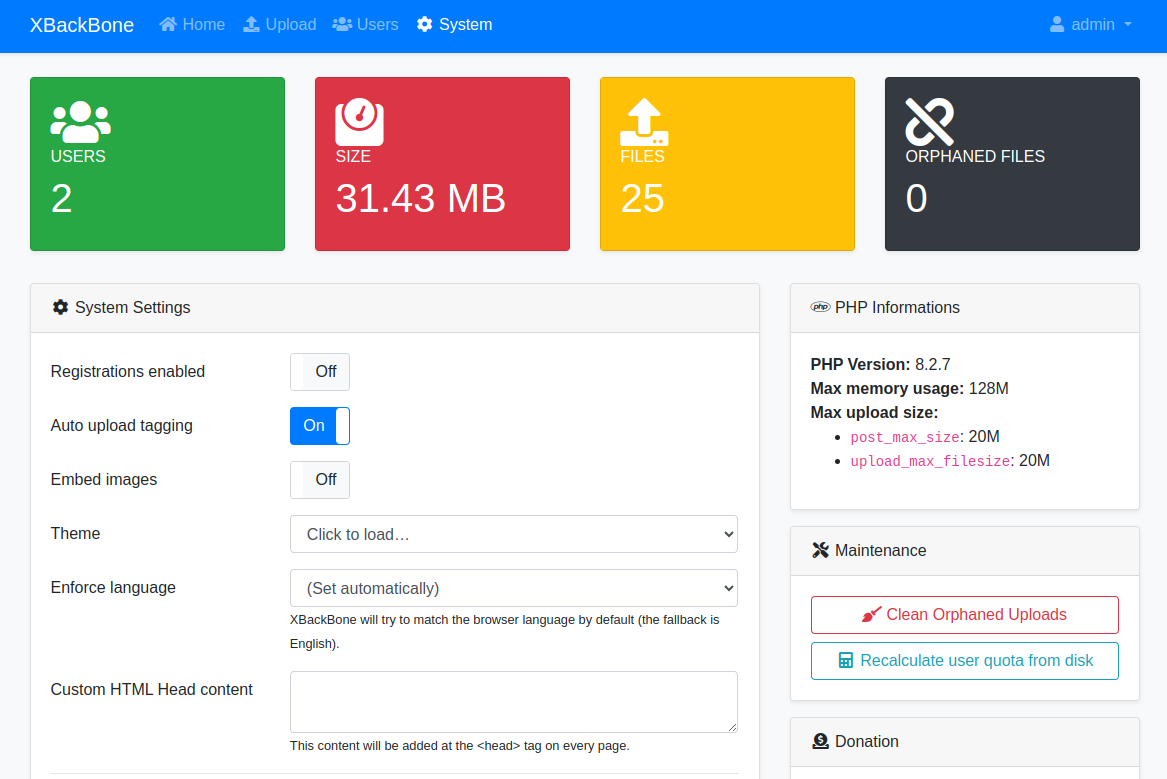
Fast and easy self-hosted software for cloud file sharing
Here is an excellent open source software package for everyone who wants to self-host a simple file sharing cloud service. Perhaps you need a file sharing system for personal use, for your family or for a small team, but above … Read the story...
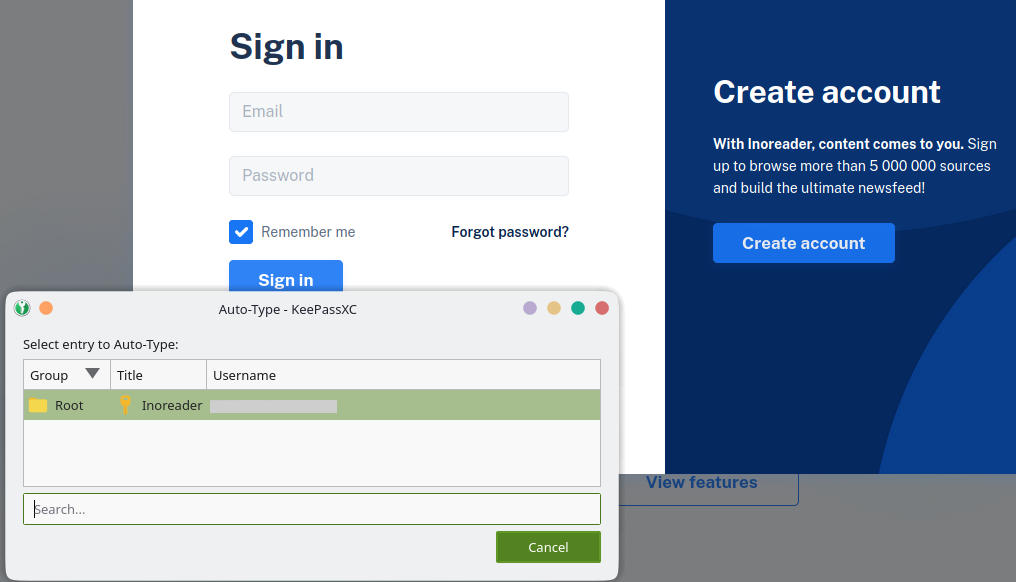
How to use long and secure passwords without typing a single character
If you are not a big fan of long, unique passwords or perhaps are reluctant ever type passwords again, this is for you. I will show you a method that lets you do exactly what the cybersecurity experts have been … Read the story...
11 Key Data Protection and Safety Principles
Data protection and the safety of personal information are incredibly important topics, especially in the digital age.
As technology continues to evolve and become more integrated into our lives, our data becomes increasingly vulnerable to cybercrime, identity theft, and other … Read the story...
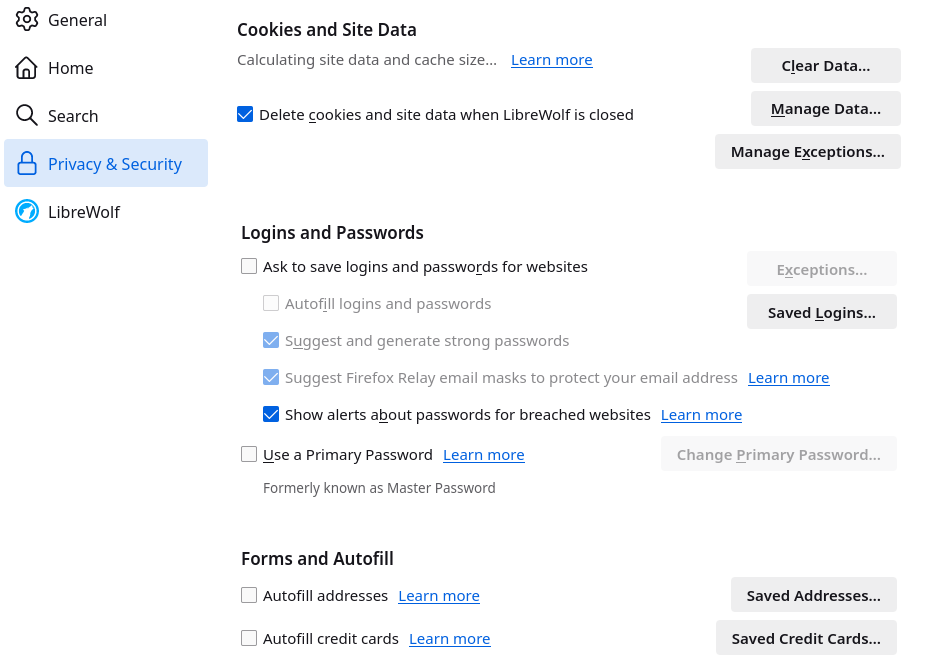
Has security and privacy in web browsers improved since the last year?
Security and privacy features in a number of web browsers have improved since the last time we checked a year ago. Since most browser developers claim that their browser is secure and protects your private data from tracking, the valuable … Read the story...
10 cornerstones for managing cyber security
I recently read a book titled Cyber Crisis that has a mission to convince every business manager and a person who owns a phone, computer, game console or an electronics device that cybersecurity is everyone’s business. The author Eric Cole, … Read the story...
Cybersecurity trends for small businesses and homes for 2023
While small organizations and home computer users continually learn more about cybersecurity, information technology develops as well. Managers can adopt the latest tools to protect important business data within organizations and family heads can protect sensitive personal data at homes. … Read the story...