Everyone who has a phone, tablet or PC uses a web browser more than she realizes. In many cases, banking, paying purchases with a credit/debit card, booking health related appointments, reading news, watching movies, and many more services are available … Read the story...
Author: Sommet
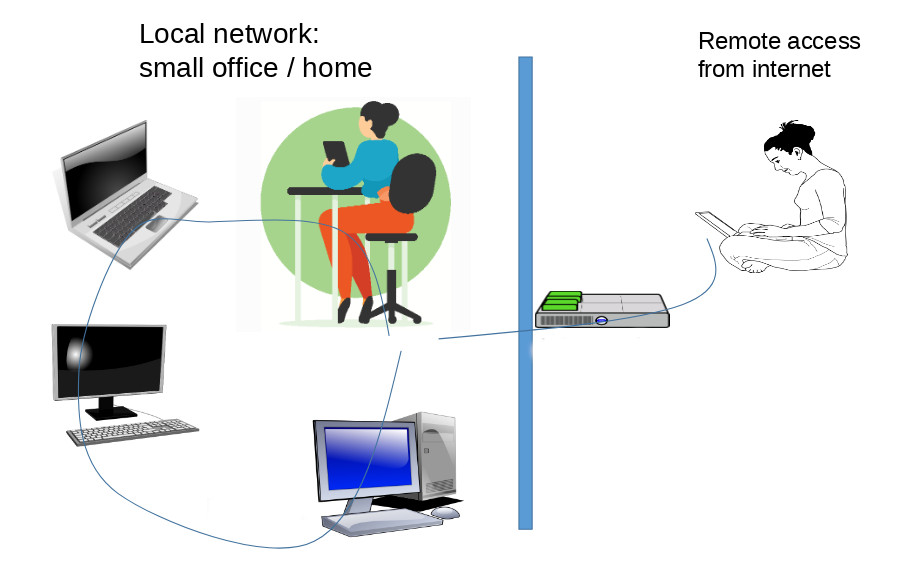
How to install and configure Dnsmasq for your network – remote access option included
Our home office network had gradually grown to the point that no one could remember the IP addresses of all devices. All the connected PCs, phones, tablets, and other devices had to be assigned names so that, for instance, a … Read the story...
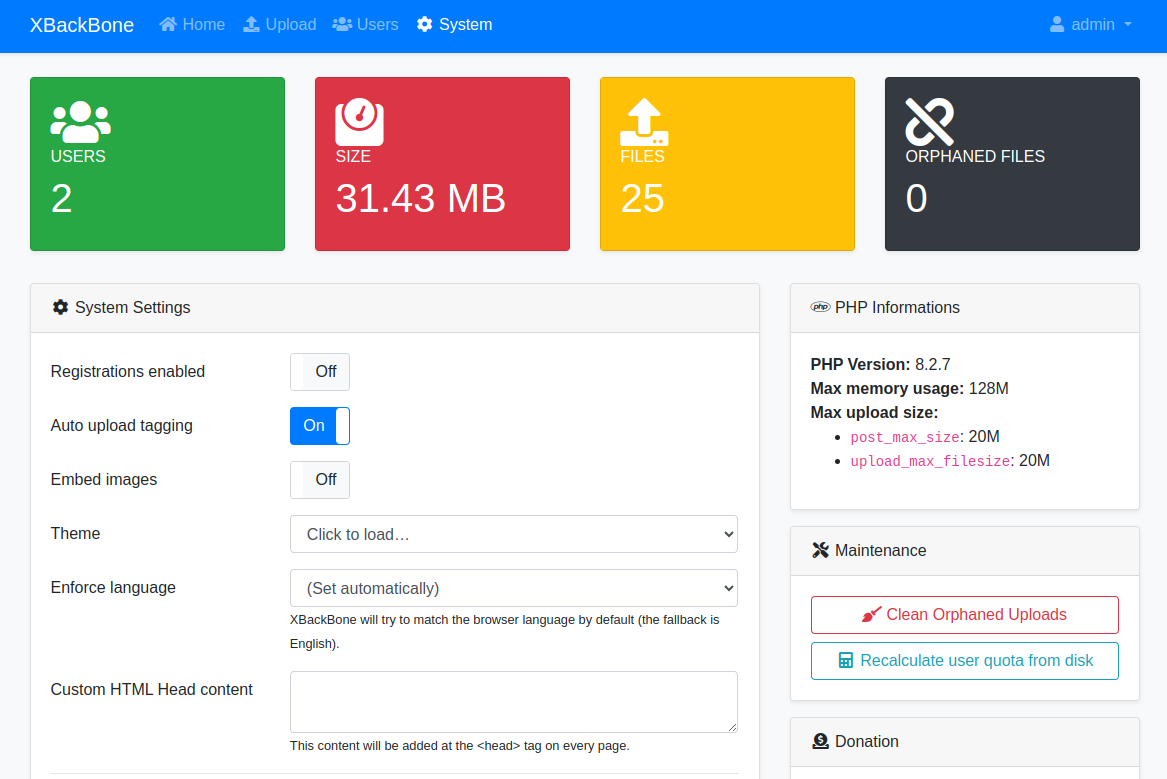
Fast and easy self-hosted software for cloud file sharing
Here is an excellent open source software package for everyone who wants to self-host a simple file sharing cloud service. Perhaps you need a file sharing system for personal use, for your family or for a small team, but above … Read the story...
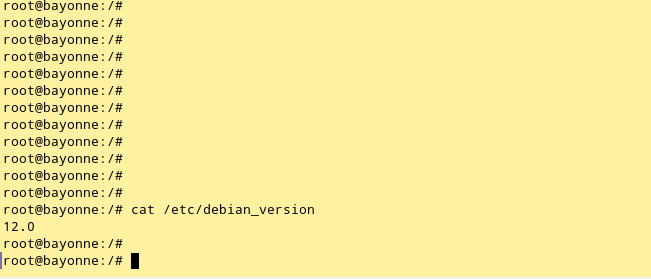
How to upgrade to Debian 12, and tips for troubleshooting problems in LAMP
Debian 12 (Bookworm) was released in June 2023 for Linux computers. The new version features a massive number of updates, such as a new Linux kernel, new PHP version, LibreOffice and much more. Upgrading an operating system to a … Read the story...
This business is driving tech industry to the era of AI
Follow the money. It is the traditional advice for everyone who wants to understand why someone is doing something that is not obvious. If I ask: why are big and small technology businesses collecting personal data of people and tracking … Read the story...
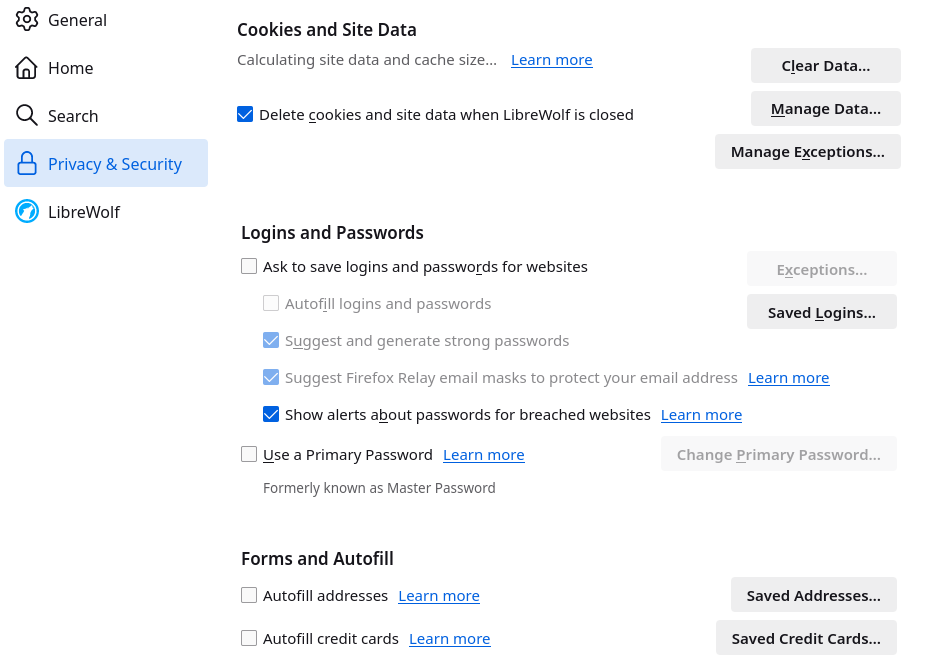
Has security and privacy in web browsers improved since the last year?
Security and privacy features in a number of web browsers have improved since the last time we checked a year ago. Since most browser developers claim that their browser is secure and protects your private data from tracking, the valuable … Read the story...
How does a small business recover from a cyber security incident?
The mantra of cyber security experts is that you shouldn’t make plans thinking if you are hacked, but plan for recovery when you are hacked. Sure, according to studies and statistics it is practically inevitable that especially small … Read the story...
The most successful cyber attack method is triggered by victims themselves
The nasty thing with social engineering is that the victim falls for a scam, and ultimately helps cyber criminals to achieve their goal. Typically they want to break into a large computer system or simply access the victim’s bank account. … Read the story...
Advertisers secretly collect email addresses from web page login forms
When you fill in a form or login to a web page, you probably expect that only the web service where you want to sign in gets your email address and password. Unfortunately, ad tech businesses that track people on … Read the story...
Study: Mobile apps can snatch your data before asking for permission
Researchers at Oxford University have analyzed a large number of applications developed for Android and iPhone mobile phones. There are many studies that have examined what the mobile operating systems (Android or Apple iOS) do with user data, but apps … Read the story...