While small organizations and home computer users continually learn more about cybersecurity, information technology develops as well. Managers can adopt the latest tools to protect important business data within organizations and family heads can protect sensitive personal data at homes. Cybercriminals, however, have access to the same technologies as everyone else. This creates a neverending race, but when you keep up-to-date with the latest developments you improve your protection.
Here are the key security trends for 2023 for small organizations and homes.
1. Social engineering scams will be assisted with artificial intelligence (AI), making attempts more frequent and more successful
Social engineering is a concept that refers to many types of techniques that are used to convince a victim to do something he shouldn’t do. It can be a phone call, a chat at a lobby, email message, anything that lets a cybercriminal contact a victim. The motivation is, for instance, to install a spy program on a PC, get a password, access victim’s bank account, or allow the cybercriminal enter a building. Social engineering is the most successful method for getting access into a computer system or into a physical location.
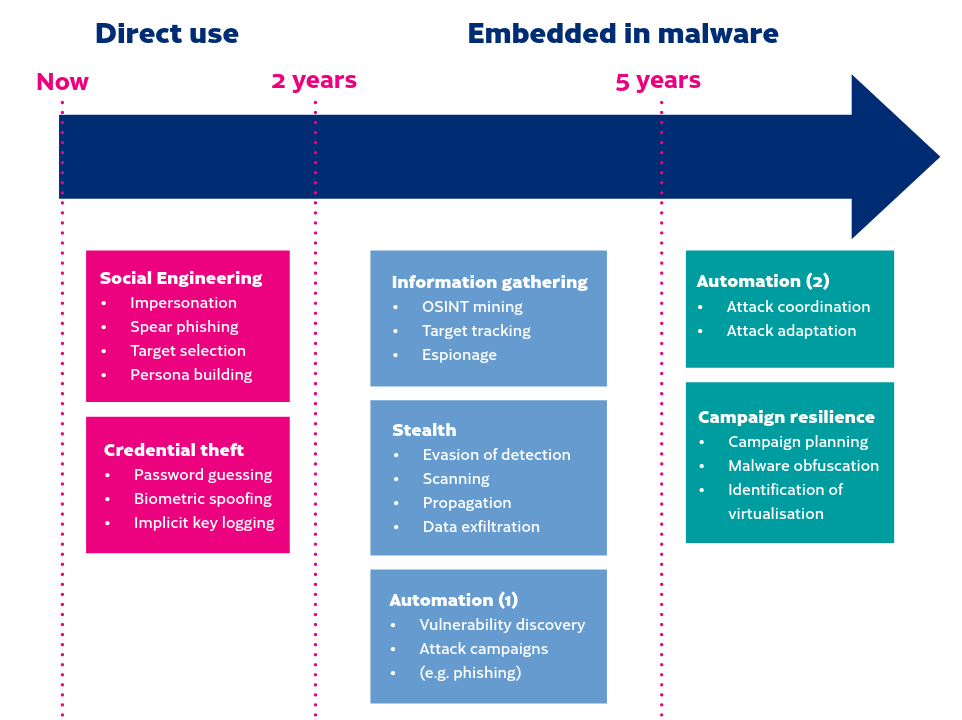
Traficom, Finland’s transport and communication agency, has published a report where AI is evaluated as a tool for cybercriminals. The conclusion in the near term is that criminals quickly adopt (and likely have already adopted) AI into their toolkits. Social engineering tasks, like phishing with email messages, faking a caller’s voice, and creating fake photos and video clips are possible already today. AI will significantly speed up cybercriminals’ work and improve the quality of fake messages, audio, photos and videos used for attacks.
2. Passkeys will become the preferred authentication method, but passwords will be used as well
Passwords have been the weak link in cybersecurity as long as they have existed. Passwords can be nearly unbreakable, but the way people use them makes them breakable. Now, security experts believe they have a solution that can replace passwords. It is called the passkey.
Each cloud service has its own method for creating user specific passkeys. Your passkeys are stored on the devices that you use for accessing the cloud service. Once a passkey is created, and you want to login to the service, you only have to unlock your device where the passkey is stored, and you are logged in. One of the risks is that if criminals get physical access to the device where a required passkey is stored, it may be possible for them to login to the service.
Passwords will have a long life span no matter which new technologies emerge. If you already don’t use a password manager, start now. You may choose a cloud based password manager service, or an application running on your PC and on mobile devices. Password managers on the cloud are convenient but attract hackers. For instance, a password manager service called Lastpass has been hacked twice. A password manager app, on the other hand, encrypts and stores your passwords on your personal computer or phone. Keepass and KeepassXC are considered secure and easy to use PC and mobile apps.
3. Complicated authentication methods will seriously annoy people
Cybersecurity is a neverending race between good guys and bad guys. Good guys try to adopt the latest technology that protects them from attacks, but after enough of trial and error the bad guys circumvent the new roadblock and enter the good guys’ system, anyhow. Banks are doing just this, and perhaps heading the wrong way. Our small business has bank accounts in three countries, and two of them have started using additional confirmations on top of existing two factor authentication. First, you login to you bank account using two factor authentication. Then you pay a bill, and have to authenticate once more. And this is not enough, the bank also sends a message that includes an additional confirmation code. Enter the code and if it matches, the bill is paid.
What next? Will the next step be codes printed on paper that you have to enter after two factor authentication, an additional authentication and a text message code confirmation?
Large organizations are deploying a technique known as zero trust security for their networks. It certainly improves security, but it also increases friction for users who have to access the system.
While all initiatives of banks and other large organizations to increase our cybersecurity are appreciated, it is time to sit down, cool down, and think long term. The multi-multi-factor-authentication methods that banks have chosen and the zero trust strategy in large organizations can’t work in the long run. They create too many roadblocks for users who will simply stop using the services if nothing better isn’t available.
4. Create a backup plan for your key social media channels – the popular ones will face big changes
Some popular social media services will change (for better or for worse) during 2023. For instance, Facebook’s founder Mark Zuckerberg has decided to invest in metaverse, and the leader of the electric car company Tesla Elon Musk has decided to renew Twitter into an absolute free speech channel. These services are not doing well at the moment, but they will survive and continue making money from users’ data and form advertisements. Many people are looking for alternative social media services, such as Mastodon that has attracted millions of Twitter users in a few weeks alone.
The thing that none of the popular social media and cloud services has been able to resolve properly is security in a user friendly way. Frankly, many are screwing up security and authentication. Some users never encounter problems, but users who travel or users who are a bit more privacy-aware tend to have problems with accessing their accounts. The services are using automated (likely AI) tools that for one reason or another lock users out of his or her account. Sure, it is possible to contact support, but after doing it a few times, users go somewhere else.
Small businesses and home users should have a plan B. For instance, if your Facebook, Google, or Twitter account is locked without any obvious reason, where do you go? If your preferred social media channel doesn’t succeed with its transformation, but it becomes a ghost town, where do you go?
5. Protecting private data will be even more crucial for personal security
Artificial intelligence (AI) will be used good and bad purposes. Cybercriminals are likely use the technology for selecting targets and for tailoring attacks for the targets who have generously published enough personal data on the internet. People who are avid users of Facebook, Linkedin, Snapchat, and other social media services may not realize that publishing plenty of personal data can be a security risk. For instance, letting the world know that your house is empty for two weeks because you are on a beach in Mauritius, unveiling your phone number, age and address are valuable pieces of information for someone who is specialized in house robberies or is preparing a personalized phishing attack.
One of the best ways to protect personal information is to consider if your next phone could be a product without Google services. Not an iPhone, not an Android phone, but a product that can run Android applications, and doesn’t leak personal data to Google or to anyone else. Examples of such ge-googled phones are Murena, Volla, and Brax2.
Another easy way to protect personal data is to check where a cloud service you are about sign up is based in. If the cloud service is operating in an EU country, the EU regulation enforces the service to protect users and their data. In other regions, personal data may be packaged, profiled and sold to other parties.
While small organizations and home computer users must keep themselves up-to-date with cybersecurity, large organizations that provide cloud services shouldn’t adopt too complex security methods. Three or four factor authentication won’t solve problems if users reject the service. If you want to prepared for the worst, here is a good starting point.