The nasty thing with social engineering is that the victim falls for a scam, and ultimately helps cyber criminals to achieve their goal. Typically they want to break into a large computer system or simply access the victim’s bank account. … Read the story...
Tag: hacker
We are doomed: cyber arms race affects our daily life and work
The book This Is How They Tell Me the World Ends: The Cyberweapons Arms Race is both fabulously entertaining and scary to read. The author, The New York Times journalist Nicole Perlroth, spent seven years researching and talking to hackers, … Read the story...
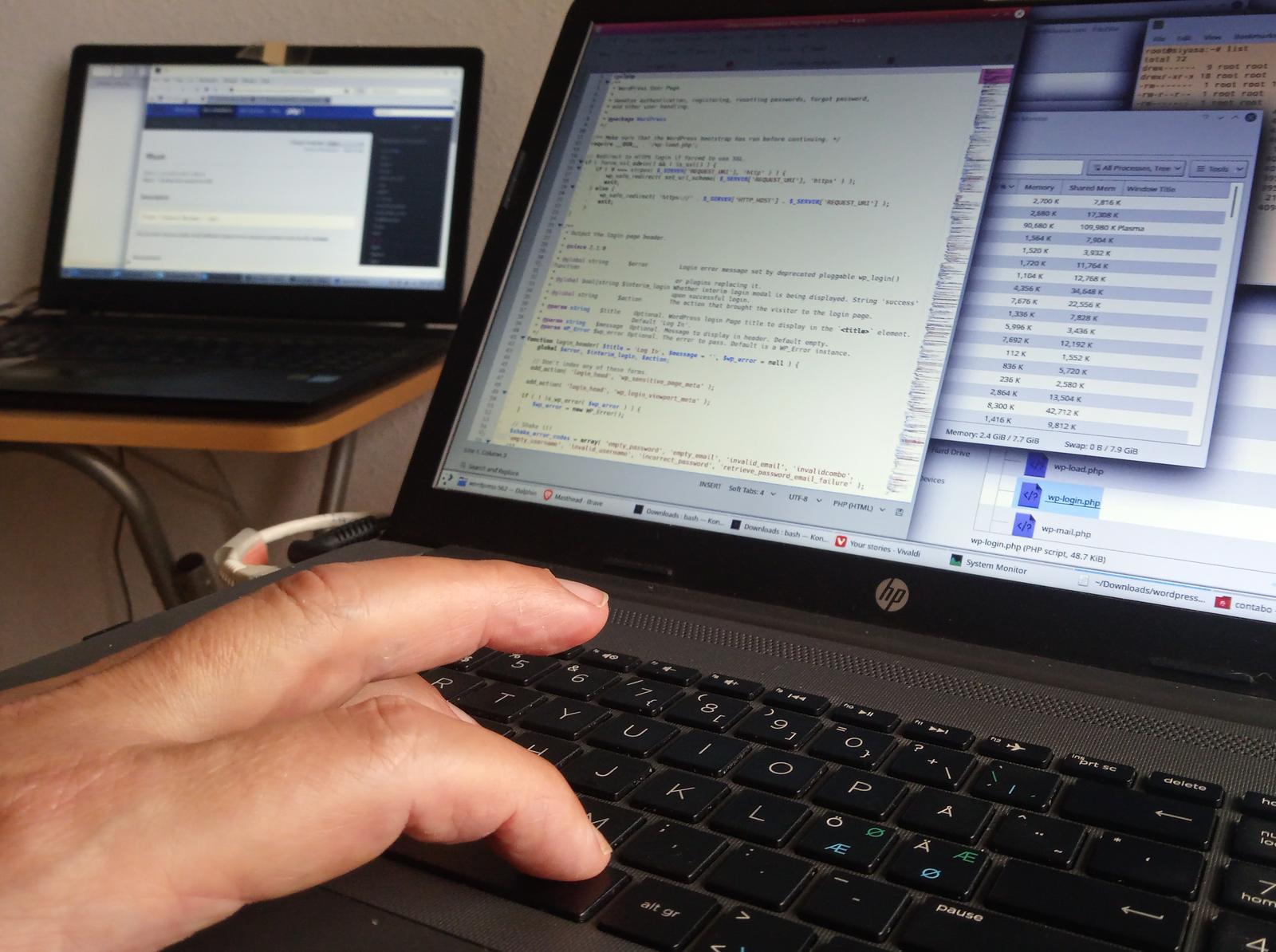
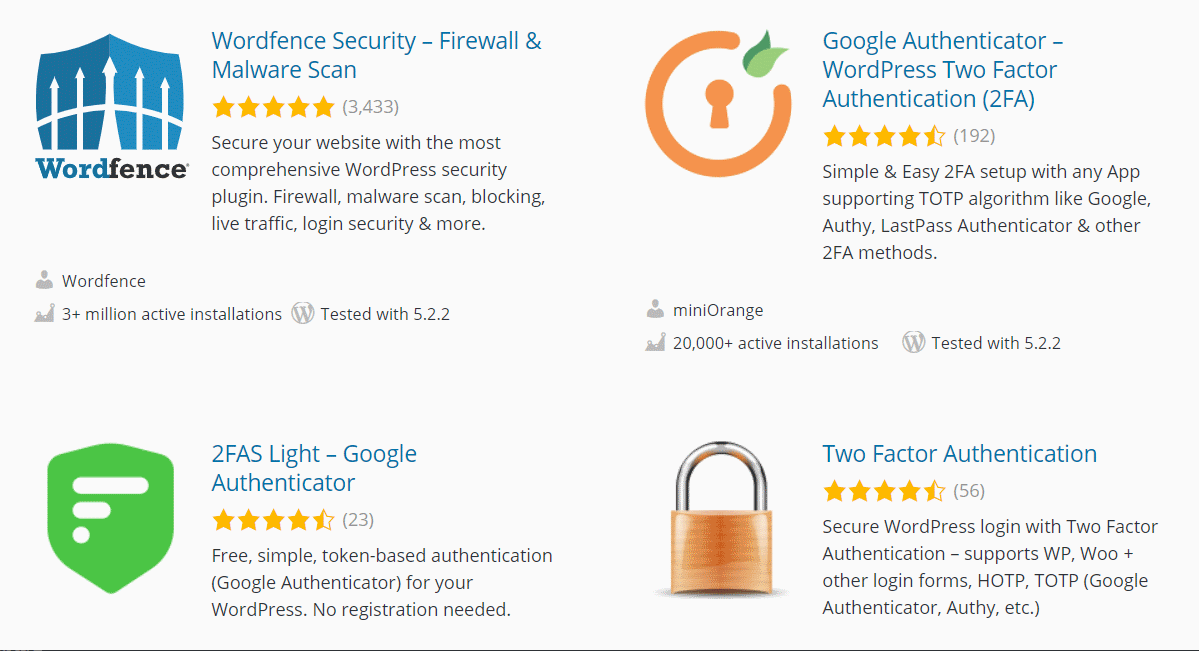
WordPress security settings for beginners (without having to know technical details)
WordPress is the world’s most popular software for building web sites and for publishing on the internet. This fact makes it the number one target for hackers. Every self-hosted WordPress admin, even if only running a simple blog, should take … Read the story...
A large botnet consisting of hacked WordPress servers is a steady business for shady entrepreneurs
The world’s most popular content management system WordPress is also the world’s most popular target for hackers. Creative hackers have established profitable businesses whose costs are paid by others.
Enterprising hackers have created a new online business that costs them … Read the story...
Security tips for remote workers, digital nomads and freelancers who travel and require 24/7 internet access
Professionals who work and travel appreciate the moment when they get access to a Wi-Fi router with fast internet access. Security experts have warned us for years not to connect to random Wi-Fi hotspots, especially, if the communication isn’t encrypted. … Read the story...
90 percent of hacked web sites were powered by WordPress
WordPress is so popular software package for online publications, e-commerce, business sites, blogs, and all types of web sites that it has the major problem that comes with success: hackers. Sucuri, a business specialized in web site security, analyzed infected … Read the story...
Cryptocurrency hackers earned $20M with 51-percent attacks in 2018
From: The Next Web
Powerful attacks on blockchains are increasing. So far this year, hackers have executed a minimum of five separate 51-percent attacks on cryptocurrency projects, with profits amounting to almost $20 million. This represents an annual success rate … Read the story...