The suspect believed to be behind an attack against one of Finland’s largest psychotherapy clinics, Vastaamo, was allegedly identified by tracing what has been believed to be untraceable #Monero transactions. #cyber
https://www.bleepingcomputer.com/news/security/vastaamo-hacker-traced-via-untraceable-monero-transactions-police-says/
Category: Communications
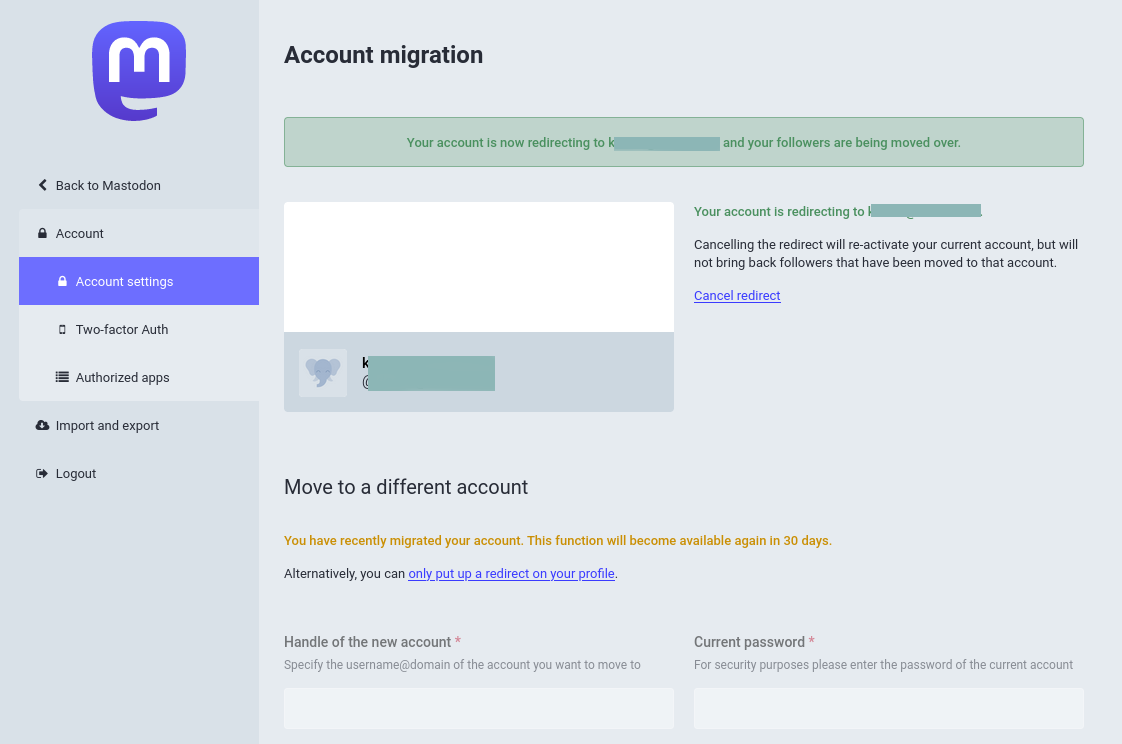
How to migrate to another Mastodon server
So I decided to move to a new Mastodon server (also known as an instance) that had terms better suitable for one of our foreign language blogs. It is really amazing that a migration function even exists in a social … Read the story...
Nextcloud self-hosters appreciate privacy and apps
Nextcloud is an open source software package for self-hosting cloud services, such as file and photo sharing, office applications, calendar, note taking, project planning, bookmarks, and news. At the end of 2021, a survey among Nextcloud users provided valuable insight … Read the story...
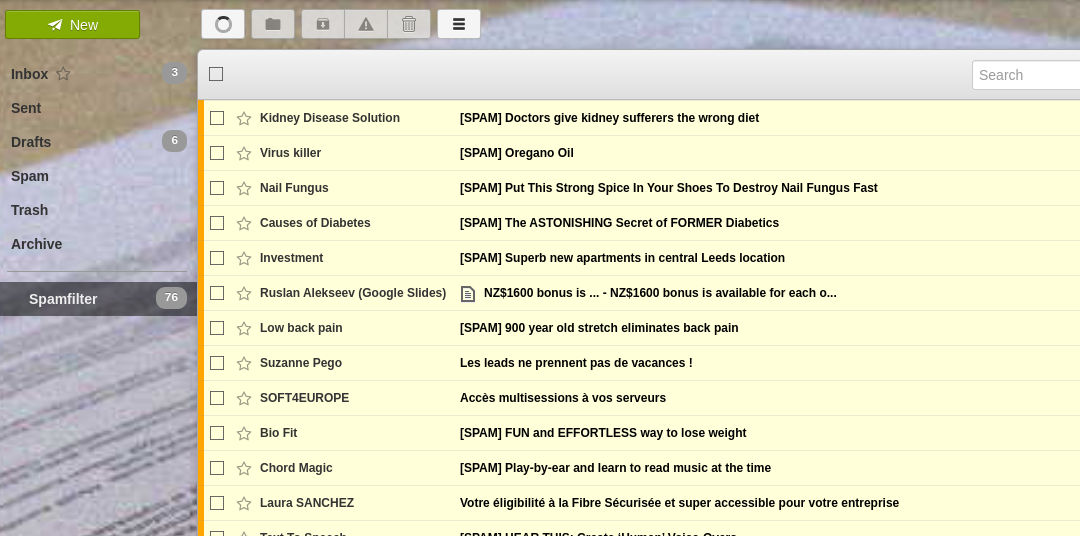
How to filter messages hosted by any email server
Some time ago, I caught our email hosting company reading my inbox. I access email in a web browser, and the browser status line displayed that a script was continuously polling for new messages and relaying data to another organization. … Read the story...
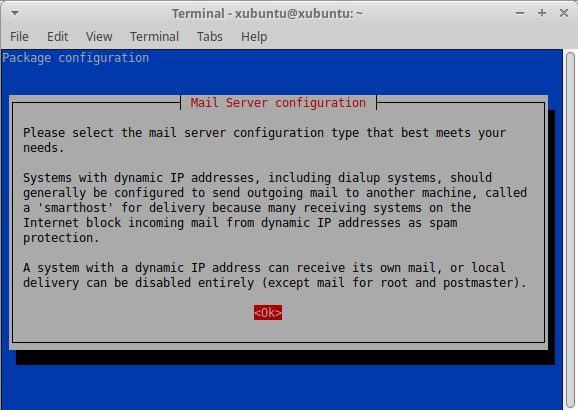
How to configure a send-only email server on Linux
Update 2021-11-07: I have written a new section that shows you how to configure exim4 if the direct SMTP send method is rejected by email providers.
Many server software applications, like WordPress and Nextcloud can send alerts and notifications to … Read the story...
Which phone doesn’t track me?
Is it possible to find a secure and privacy respecting mobile phone that doesn’t track its owner? The short answer to the question is: no, there is no such phone. Nonetheless, I believe it is valuable to understand why because … Read the story...
This is why your mobile phone is constantly being tracked
Mobile phone is one the most useful innovations of modern times. It is a remarkably valuable technology that has transformed our lives, work, and to certain extent communities all over the world. Our culture has changed as communication between people … Read the story...
How to install Rainloop webmail for accessing multiple inboxes in a browser
My problem with email used to be that I had to manage multiple email accounts because of multiple job roles I had. Since I only use webmail for getting access to all my inboxes and outboxes from any device, I … Read the story...
Goodbye Skype! I’ll miss you, but I’m getting another Voip service for privacy
Microsoft, the current owner of Skype internet telephone service, was recently caught listening to ordinary people’s phone conversations conducted on Skype.
The first case was reported in August 2019 when Microsoft utilized Skype’s automatic translation feature to listen to phone … Read the story...
Upgrade to Nextcloud version 17
Open source cloud server Nextcloud development team has released version 17 of the software. We decided to upgrade our Nextcloud 16 system to version 17, and document the required steps while doing it. Here is a guide you can follow … Read the story...