When a clever phishing message or phone call happens to be delivered to a person at the right moment, it is possible that the target follows the instructions given by cyber criminals. A recent research discovered that up to 30 percent of people may fall for phishing attempts if they … Read >
Technology predictions for 2022 and beyond: neuromining, synthetic data, cyberattacks
Recent bets for major technology developments in 2022 and beyond include metaverse, decentralized computing, and Web 3.0. If we take a look at tech trends from enterprise and security perspective, things like AI (artificial intelligence) and privacy are trending. Gartner Inc., a consultancy that advises corporations and other … Read >
Popular passwords stay the same, but there are surprising differences between countries
In 2021, the most common password in the world still is 123456. The fourth most used password is qwerty and the fifth – what else – password. Not much has changed with the most used passwords during years, but there are remarkable pieces of information in the ranking … Read >
What is the difference between metaverse and fediverse?
The universe is an extremely large and extremely complex entity, but new technology concepts metaverse and fediverse are rather complex as well. Metaverse and fediverse are so different concepts that it may not even be reasonable to compare them, but the comparison may help us understand what they are and … Read >
Android phone comparison: the best and worst products for privacy
When the first smartphones were introduced about 20 years ago by a number of telecommunication equipment vendors, the mobile device was expected to become the primary communication tool for the majority of human kind. It did. But there was something else that no one could envision 20 years ago: product … Read >
How to upgrade to Debian 11, plus tips for troubleshooting
A major new release of Debian Linux operating system is a big deal for a vast number of organizations and individuals who run Linux servers and PCs. Debian is the base software for many other Linux distributions, making its reach far wider than it seems. Debian is well documented and … Read >
Web 2.0 has been a game-changer, but where is Web 3.0?
Plenty of technologies, like augmented reality, artificial intelligence, blockchain, and speech recognition have matured to practical applications during the last few years. There are lot of communication technologies, such as peer-to-peer social media platforms, wearable devices, self-hosting, IoT (internet of things devices) that are widely used by people. So many … Read >
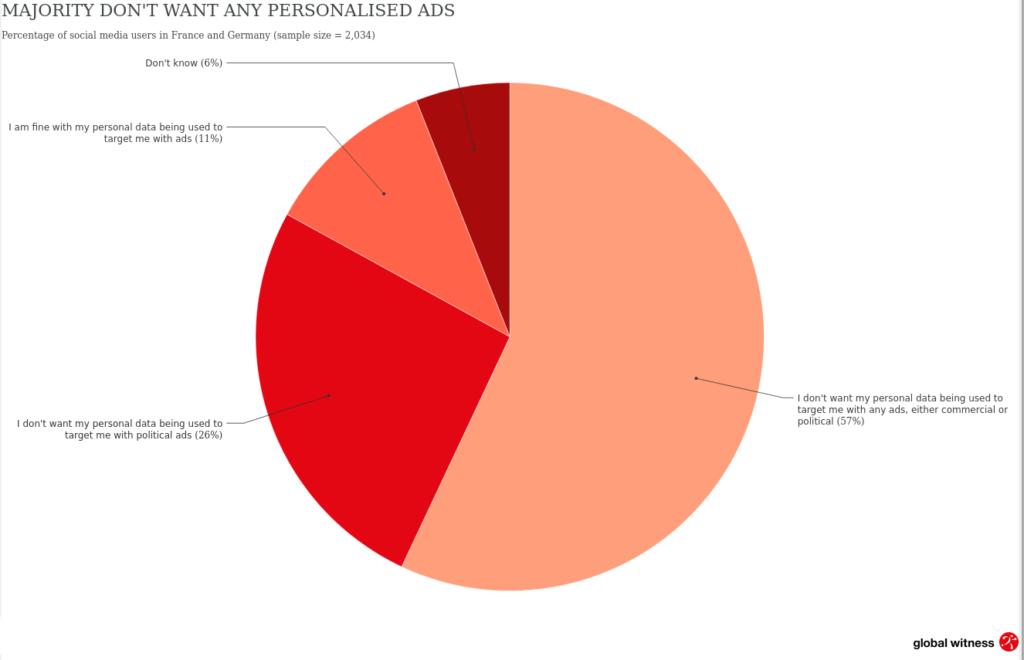
Only 11 percent of internet users in Europe are fine with personalised ads
As long as enterprises have tracked internet users’ behavior and life, marketeers have explained that data is needed for personalised advertisements. They claim personal ads, rather than broadcasting the same ads to all people like on television, are beneficial for everyone. Why is it … Read >
Improve your PC security with task-specific browsers
When we are using a PC – a Windows, Mac, or Linux computer – web browsers tend to be one of the most accessed applications. Unfortunately, web browsers are frequent attack targets because they can run Javascript programs on a PC, download new software on a PC, and access files … Read >
How to set up a self-hosted file storage with Filerun
More and more privacy and cybersecurity-aware people are looking for alternative solutions to popular cloud file storage services like Dropbox, Google Drive, and Microsoft Onedrive. These services have plenty of functionality, but they don’t respect your privacy, and they are also lucrative targets for hackers. Setting up and hosting your … Read >