A missing network driver is probably the nastiest problem you can encounter when installing Linux operating system on a computer. Since you can’t connect to the internet, you can’t download the missing firmware, and can’t find advice from other Linux users who have experienced the same faith. Here are a few tips how to survive, and complete the Linux installation successfully.
UPDATE: this How-to article was updated on November 16, 2020 (the original was published on July 28, 2019). The new troubleshooting section addresses problems with Debian 10 Buster and Realtek Wi-Fi firmware (at the end of this article).
First thing to do is to get access to another computer that is connected to the internet. Alternatively, if you happen to have an Ethernet cable and your router has a port for it, you can hook a cable from your computer to the router for internet access (I didn’t have a cable nor a port in the router).
In this article, I’ll explain how I solved the missing Wi-Fi driver problem when I was installing Debian 8 (Jessie).
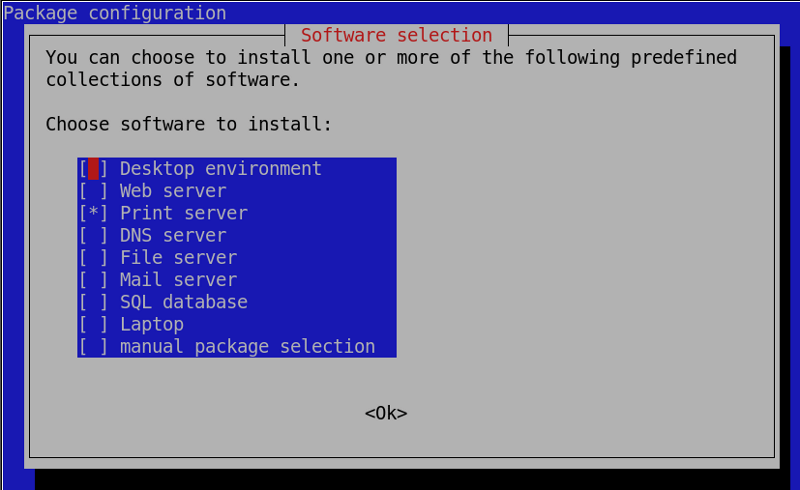
The trouble started when the Debian installation process displayed the following error message:
“Some of your hardware needs non-free firmware files to operate. The firmware can be loaded from removable media, such as USB stick or floppy.
The missing firmware files are: rtlwifi/rtl8723befw.bin”
If you are wondering what a floppy is, don’t worry. It is storage media used in ancient computers only. USB memory stick is the best choice for transferring the missing files from another computer to the Linux machine.
It is time to use another computer for searching for the missing drivers. The keyword is “rtl8723befw.bin”, or whatever your error message displayed. I discovered the missing Realtek drivers at Debian web site (each Debian version has its own firmware packages).
Copy the downloaded .deb file to a USB stick.
Insert the USB stick into the Linux computer.
If you still have the missing firmware error message on the screen, you can answer:
Yes to “Load missing firmware from removable media?”
Answering Yes didn’t work for me, so I continued the installation process to the end. Once the system was installed and running, I solved the Wi-Fi problem. Here is how.
Copy the .deb file from the USB stick into the Linux computer.
Open Terminal app.
Enter command: dpkg -i path/filename
(where path is the directory where you copied the .deb file and filename is the name of the .deb file)
If you get error messages about access rights, enter su or sudo command to login as root.
Why not choose the easy way, and simply use apt-get for finding and installing the missing software packages? Well, since I didn’t have internet access on the Linux computer, I couldn’t rely on (apt, apt-get, aptitude) online repositories.
Realtek Wi-Fi firmware on Debian 10 Buster computer
Debian 10 (Buster) installation process doesn’t include Wi-Fi driver software for Realtek hardware. The nasty thing is that installation just ignores Wi-Fi altogether and doesn’t give a hint what is wrong.
First, ensure you have the following packages in your system:
- firmware-linux
- firmware-linux-nonfree
- firmware-realtek (I chose the latest version labeled …_bpo10… )
I had to download the packages from Debian repository manually using another PC, and install them using dpkg command because I didn’t have network connection. If you have wired internet connection on your computer, you can use apt command to install the packages. If you have network connection, check the following lines in /etc/apt/sources.list
deb http://deb.debian.org/debian buster main contrib non-free
deb-src http://deb.debian.org/debian buster main contrib non-free
deb http://deb.debian.org/debian buster-backports main contrib non-free
deb-src http://deb.debian.org/debian buster-backports main contrib non-fr
ee
The important thing is that the words contrib and non-free are included. Now apt or apt-get should be able to install the firmware packages.
After installing the packages, reboot your machine and check if Wi-Fi has woken up to scan available signals.
If Wi-Fi still doesn’t work, you can test if the reason is an unsigned driver software used by the wireless hardware. By default, Debian 10 installs and activates Secure Boot mode. It uses UEFI interface that requires all firmware to be signed. This is a design decision to prevent malware posing as drivers to run during boot.
To test if the Wi-Fi problem has to do with Secure Boot, you can disable it with MOK tool:
Run the command:mokutil --disable-validation
Type a password from 8 to 16 characters. Write it down on a piece of paper – yes, just do it.
Reboot.
Follow the reboot closely, and be ready to hit a key when prompted. You have to be fast to be able to open the tool.
Once in the tool, select Change Secure Boot state.
The tool asks random characters from your password one by one. Type the correct character, push Enter, and type the next and so on.
Select “Yes”.
Select “Reboot”.
Now, re-check you Wi-Fi. If you have a signal, the reason was an unsigned driver that won’t start on a computer running in Secure Boot mode.
All right, we have discovered the problem, but let’s take a moment to think about the long-term solution. The options are:
A) Run the computer without Secure Boot. This solution has its risks. For instance, NSA recommends Secure Boot.
B) Return to Secure Boot mode: mokutil --enable-validation
and find a way to sign the driver you need for your computer to function. Here is how NSA answers the question how to do it:
How do I make a driver compatible with Secure Boot?
Many Linux anti-malware solutions include drivers that do not have Secure Boot signatures. To solve the problem, do not disable Secure Boot. Instead, create an RSA 2048 public key certificate. Use the corresponding private key to sign the driver using sbsigntool, pesign, or similar. Switch to Secure Boot custom/user mode in the UEFI configuration, and then append the custom certificate into the machine’s DB using UEFI configuration, Keytool, or similar. Do not make changes to the PK, KEK, or DBX. The driver should be validated by the custom certificate following the next boot. Remember to sign updates to the driver before distributing to endpoints.